3615 Incident (3)
Category: Forensic
Points: 186
Description: Une victime de plus tombée sous le coup d’un rançongiciel. Le paiement de la rançon n’est pas envisagée vu le montant demandé. Vous êtes appelé pour essayer de restaurer les fichiers chiffrés. Déchiffrez le fichier "flag.docx" ci-joint!
Files: data
TL;DR
The file is decrypted using the key found in step 2.
Methodology
We have a file encrypted by the ransomware, the decryption key and we know the encryption method which is AES_CTR thanks to the ransomware code.
Agreement of some Google dorks we easily find a script to decrypt a file thanks to python.
>_ cat decrypt.py#!/usr/bin/env python3
import binascii
import os
from Crypto.Cipher import AES
from Crypto.Util import Counter
def int_of_string(s):
return int(binascii.hexlify(s), 16)
def encrypt_message(key, plaintext):
iv = os.urandom(16)
ctr = Counter.new(128, initial_value=int_of_string(iv))
aes = AES.new(key, AES.MODE_CTR, counter=ctr)
return iv + aes.encrypt(plaintext)
def decrypt_message(key, ciphertext):
iv = ciphertext[:16]
ctr = Counter.new(128, initial_value=int_of_string(iv))
aes = AES.new(key, AES.MODE_CTR, counter=ctr)
return aes.decrypt(ciphertext[16:])
if __name__ == "__main__":
file = open("data", 'rb')
data = file.read()
out = decrypt_message("95511870061fb3a2899aa6b2dc9838aa", data)
o = open("decrypted", 'wb')
o.write(out)
o.close()We run the script:
>_ ./decrypt.py
>_ file decrypted
decrypted: Microsoft Word 2007+We have a docx, all right!
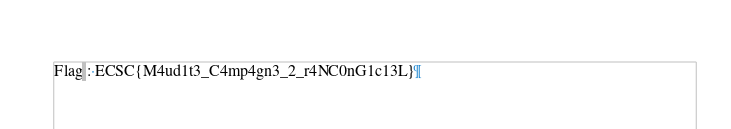
FLAG_IS:
ECSC{M4ud1t3_C4mp4gn3_2_r4NC0nG1c13L}
